
BLE
Bluetooth Low Energy is the perfect wireless technology to connect devices in a dependable, low-power and safe way.
Automatically unlocking your car when you walk up to it. Paying for groceries without struggling to find your wallet. Sending health data collected by a wearable or even implantable device directly to your smartphone. All without needing to worry about privacy or security.
Read more about the use of Bluetooth in medical devices.
Those are the ways in which the Internet of things (IoT) can make our lives easier. It relies on a backbone of small, battery-powered devices such as beacons and sensors – connected to each other and to the cloud.
In order to realize those connections, the technology must be compatible with:
- the design constraints of IoT devices: small and highly integrated form factor, reliable and ultra-low-power operation
- the existing networking technology in server devices such as smartphones
Bluetooth Low Energy (BLE) fits the description. And new capabilities for Bluetooth high-accuracy distance measurement/channel sounding (BT HADM/CS) can be added. This expands the current use cases to next-gen wireless secure access and proximity solutions. Examples are item finding, asset tracking, real-time location systems (RTLS) and indoor positioning systems (IPS).
This is what imec’s experts are working on, both on a hardware and software level.

Next-gen BLE is an important enabler for IoT applications such as smart locks.
Bluetooth Low Energy hardware design
Imec’s BLE radio designs and IP enable an on-chip transceiver. That’s ideal for IoT implementations because of its best-in-class performance at the world’s lowest power consumption.
Its key features are:
- multi-standard 2.4 GHz analog front-end
- novel phase-tracking receiver architecture
- advanced digital transmitter
- low cost
- ultra-low power consumption
- best-in-class sensitivity
- robustness to interference
- designed in TSMC 40nm ULP for 0.8V nominal supply
Download the leaflet for a complete overview.

Imec’s up-to-10-cm-accurate and secure localization solution based on BLE.
This BLE design and IP is accessible through licensing. An evaluation board is available upon your request.
Do you want additional assistance in developing your IoT hardware solution? We are ready to assist you with:
- system and IC implementation
- antenna design with regard to form factor, materials, and packaging
- design, prototyping, and low-volume manufacturing of custom low-power radio ASICs
- access to high-volume production by our foundry partners
Bluetooth Low Energy algorithms: high-accuracy distance measurement/channel sounding for the IoT
The ability to use Bluetooth signals for distance measurement presents exciting opportunities. Examples are applications such as location-based secure access and proximity marketing. However, current standards fall short in terms of both accuracy and security.
Current BLE-ranging solutions only reach an accuracy of about 3 meters. They use the received signal strength (RSSI) method, which especially struggles in challenging (indoor) environments with lots of reflections.
Imec’s ranging solution uses a combination of a phase-based distance estimation protocol and advanced signal processing. This enables the system to separate line-of-sight from multipath signals. And to thereby reach sub-meter accuracy – even up to 10 cm if multiple antennas are used.
3 reasons why Bluetooth channel sounding will transform distance measurement and its applications
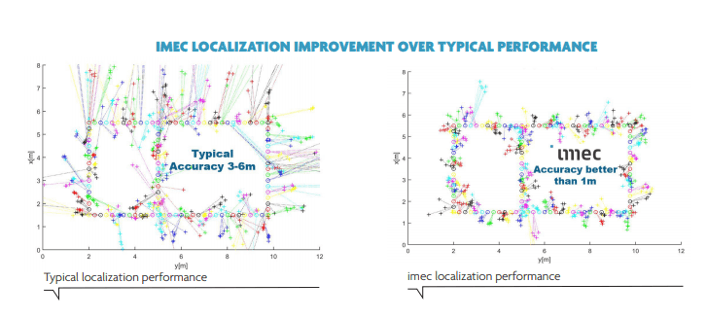
What’s more, imec’s secure distance bounding protocol ensures that it’s impossible to falsify the proximity of a device. Which means so-called location spoofing or relay attacks can be averted. Download our whitepaper to learn more.
Key features of imec’s BLE algorithms for IoT applications:
- up to 10-cm ranging accuracy
- suitable for standard 2.4 GHz radio
- secured against relay attacks
- requires low processing power
Download the leaflet to explore the details. Or contact us to discuss your challenge.












