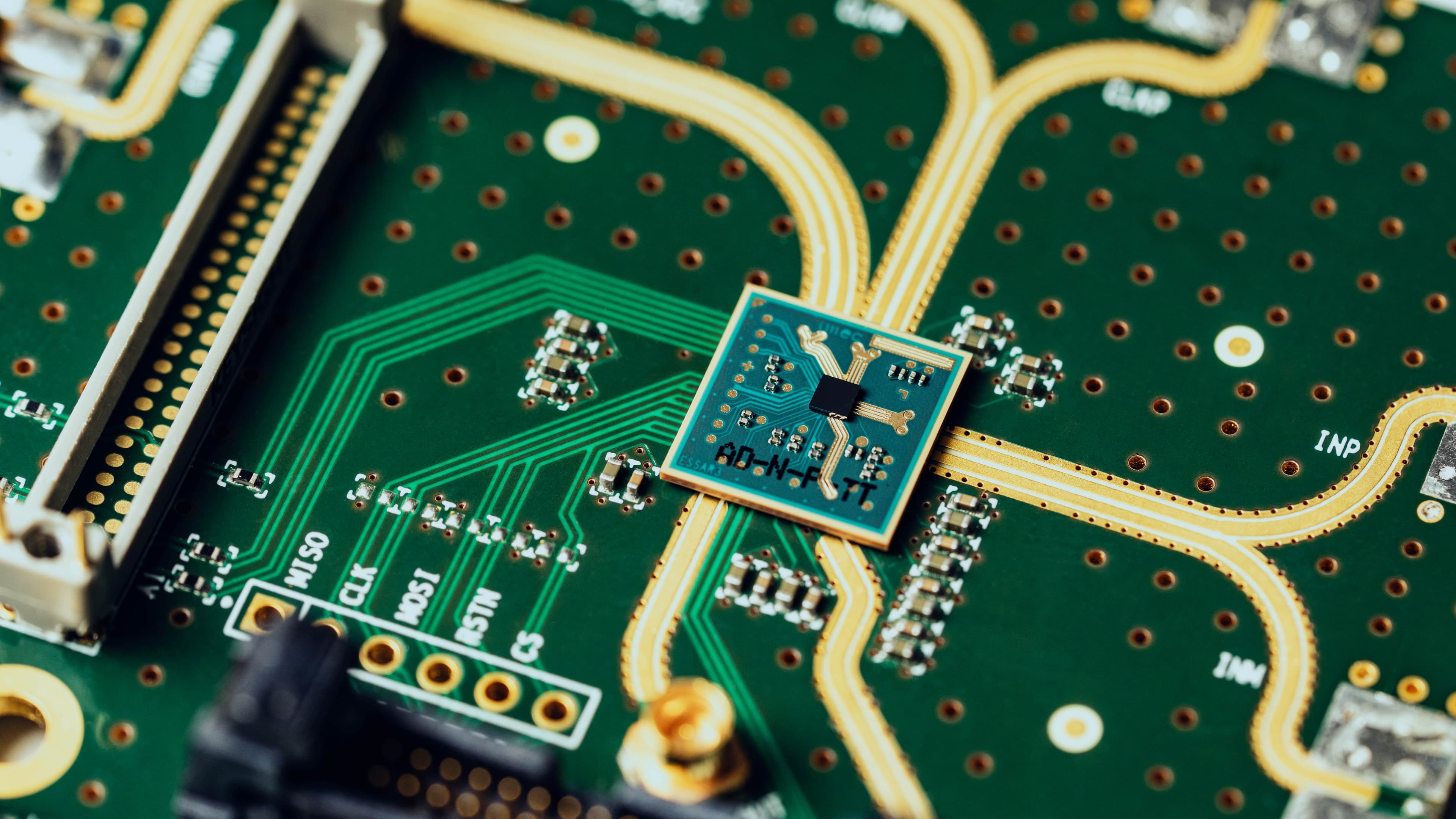
A team of researchers at COSIC, an imec research group at the University of Leuven (Belgium), has uncovered serious security flaws in the Passive Keyless Entry and Start (PKES) system used by some luxury vehicles. The study shows that the key fob used by the Tesla Model S is using out-dated and inadequate proprietary cryptography. An adversary can abuse these flaws to clone a key fob in a matter of seconds, allowing to unlock and start the vehicle. Other manufacturers that may be affected include McLaren, Karma Automotive and Triumph Motorcycles as they are all using a PKES system developed by Pektron.
High-end vehicles are often equipped with a Passive Keyless Entry and Start (PKES) system. These PKES systems allow to unlock and start the vehicle based on the physical proximity of a paired key fob; no user interaction is required. This research shows that if one is not careful, enhanced convenience increases the attack surface.
The goal of our research was to evaluate the resistance of a modern day PKES system to different types of attacks. We have completely reverse engineered the PKES system used in the Tesla Model S. Our research shows that this system is using the outdated proprietary DST40 cipher; in 2005 it has already been shown that the key is too short.
Using DST40 today has grave security implications: we can recover the cryptographic key in a matter of seconds using advanced key search techniques. Once the cryptographic key is recovered we can impersonate the key fob, allowing us to unlock and start the vehicle.
Researchers have already demonstrated that PKES systems are particularly vulnerable to relay attacks. In this type of attack two adversaries relay the short-range communication over a long-range communication channel. Recent news reports and home security videos have shown that relay attacks are being used in the real world to steal luxury vehicles. Distance bounding mechanisms are gradually being deployed to preclude relay attacks.
Our attack is easier to execute than a relay attack: we don’t have to be close to the car and key fob at the same time. Furthermore, we only require a few seconds close to the key fob to create a perfect clone that can be used to unlock and start the car as many times as we like.
We have verified our attack in practice on two Tesla Model S vehicles and first reported the issue to Tesla on August 31, 2017 under a responsible disclosure procedure. Tesla confirmed our findings and awarded us with a bounty of USD 10.000. We have also contacted the other car manufacturers who use key fobs from Pektron, none of which have acknowledged the vulnerability.
Our research results in a better understanding of automotive security and helps Tesla to address the security issues. It can also help the industry to improve the security of future products. Tesla Model S owners should consider using the security features that were recently added using software updates by Tesla. Specifically, they should disable passive entry and enable the pin to drive features.
While we cannot confirm that the vulnerability affects McLaren, Karma and Triumph without access to these vehicles, owners should consider placing their key fob in a metal container (a Faraday cage) to block radio signals. These short-term countermeasures may not preclude all attacks but should make it harder to successfully conduct an attack in practice.
Contacts
Lennert Wouters (ESAT/COSIC)
lennert.wouters@esat.kuleuven.be
+32 474 598 588
Prof. Bart Preneel (ESAT/COSIC)
bart.preneel@esat.kuleuven.be
+32 494 567 641
Published on:
10 September 2018